A study by Australian security consultant SEC Consult found that embedded devices from many manufacturers, including major ones, use the same HTTPS certificate and private key. On November 25, CERT/CC of Carnegie Mellon University issued security information and called attention to the risk of information being leaked by a man-in-the-middle attack that interrupts HTTPS communication.
As part of an internal study, SEC Consult analyzed the firmware images of nearly 4,000 embedded devices from over 70 manufacturers. As a result, it turned out that there are more than 580 private keys that are common to many devices. More than 9% of all HTTPS hosts on the web and more than 6% of SSH hosts use such private keys.
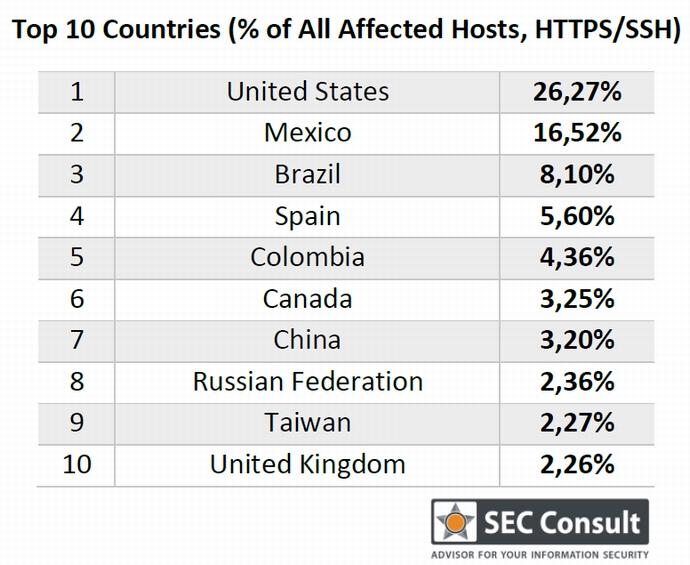
Top countries with affected HTTPS and SSH hosts (from SEC Consult)Affected products include routers, IP cameras, and VOIP phones. An SEC Consult study found vulnerabilities in more than 900 products from about 50 companies. According to CERT/CC, the vulnerability has been confirmed in products of major companies such as Cisco, General Electric (GE), and Huawei Technologies, as well as many unconfirmed manufacturers.
Although most of the same certificates and keys are reused within the same product line or manufacturer, there are some In some cases, the same certificate and key were used by multiple vendors. This is due to OEM devices using firmware developed with common SDKs and firmware provided by ISPs.
For example, certificates found in Broadcom's SDK were used in the firmware of more than 480,000 devices from multiple manufacturers, including Linksys, SEC Consult reports.
If this vulnerability is exploited, a man-in-the-middle attack can be launched to break the encryption, and important information such as login information for administrators may be leaked. The leaked information could also be used in other attacks.
CERT/CC urged individual manufacturers to inquire as they do not have a realistic solution. If possible, I advise manually replacing X.509 certificates or SSH host keys with unique ones.


