This is the second special contribution of the 2011 version of the virus software "Virus Buster 2011 Cloud" by Torend Micro Rie Nagashima.Following the introduction of the big feature, "Cloud", it is an explanation of the three new features (editorial department).
"Browser guard" that blocks malicious scripts
Last time we talked about the cloud technology "Smart Scan", but there are three other new features in the Virus Buster 2011 Cloud.
The first is "Browser Guard".This feature is a function that assists the web reputation technology that blocks dangerous websites, including phishing scam sites.
In January 2010, a zero -day attack was reported, aiming for the vulnerability of Internet Explorer (hereinafter, IE).At the beginning of the problem, the vulnerabilities existed in all versions except IE version 5 were targeted, so it was dangerous to infect a virus just by browsing a website with an unauthorized JavaScript.had.
In this case, if a website with an unauthorized JavaScript has been registered as a dangerous website in the web reputation database, the site is blocked and the user is unlikely to be dangerous.However, if you have not registered, the danger will be very high.
In order to respond to such an attack, the browser guard checks the behavior of JavaScript embedded in the HTML file, and if it contains malicious scripts, display the website before referring to the web reputation database.Block.
Figure 1 Image of browser guard
If you block, report the information on the website to the trend micro and reflect it in the web reputation database so that other users do not browse the dangerous sites.The implementation of this function allows you to block unregistered websites in the web reputation database.
Screen 1 Block dangerous access by browser guard
"Local correlation analysis" that analyzes complex infection routes on a personal computer
The second function is "local correlation analysis".Many recent viruses have the ability to guide users to dangerous websites and forcibly download one of the applications called downloaders.
In most cases, the downloader itself does not damage the computer directly.However, we try to control the user's computer to connect to another dangerous website and download various viruses (as virus A).
In such a case, the local correlation analysis of Virus Buster 2011 is not only how Virus A tried to enter the user's computer, but also "Where did the downloader who tried to download virus A entered the PC?"Analyze complex infection routes on a personal computer.
The analysis results are reported to the trend micro to prevent other users from being dangerous.A local correlation analysis that analyzes complicated infection routes can be said to be useful to cut off the viral infection.
Figure 2 Local correlation analysis to analyze the transmission route to prevent danger
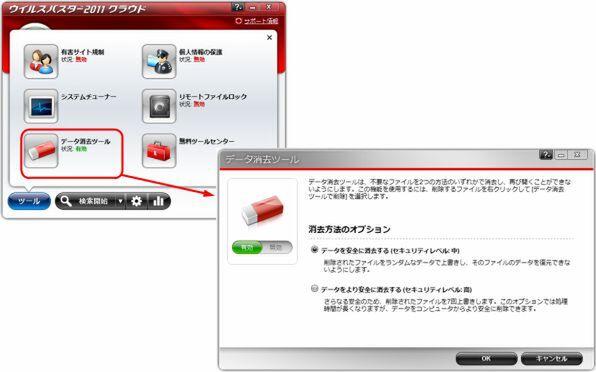
"Data erasing tool" that ensures information
And the third new feature is the "data erasure tool".It seems that more and more consumer users have been concerned about personal information since the issues of personal information leakage in companies began to attract attention.Even for personal computers used at home, personal information is stored even if the scale is different, such as the email address and the creation of an address recording with Excel.
When erasing such personal information, it is not completely erased by putting it in the "trash can" of Windows and emptying the "trash can".In many cases, it can be restored with a commercially available data recovery tool.This is composed of "management data" and "actual data", and only "management data" is deleted by emptying "trash can", that is, only file management information.is.Even if the trash can is empty, it is possible to restore data by using a special tool in an environment where "actual data" remains.
In the data erasing tools that can be made in the virus buster 2011 cloud, the actual data is overwritten seven times with meaningless data (such as repeated 0/1).In other words, it is processed so that the data cannot be read by overwriting the actual data part.This method is the US Department of Defense standards (DOD 5220).Since it is a method that matches 22-m), it can be said that it is a safe data erasing method.
Figure 3 Mechanism of data erasure tool that enable a file to be restored
In addition, many of the commercially available data erasing tools seem to use similar techniques.The data erasing tools on the market can make detailed settings, such as buying a schedule to erase the data in "My Documents" at a specific time of the week, but it is safe without additional costs.If you want to erase the data, please use it.
Screen 2 data erasing tool
Virus Buster 2011 Cloud that can be used for free for 30 days
In this way, the Virus Buster 2011 Cloud has realized both lightness and safety in the cloud technology "Smart Scan" described in the previous time, and has a new function browser guard, local correlation analysis, and data erasing to enhance safety.Tools etc. have been implemented.Of course, there are functions required for home security measures, such as spam countermeasures, fishing fraud, firewall -related, and URL filtering installed in old products.
This time, no new functions were implemented in the Mac version function, but just by purchasing one virus buster 2011 cloud, Windows, Mac, and a license system that can take up to three PCs with a combination you like.But it can be used continuously.If you are already using Virus Buster, please use the free version upgrade.
Screen 3 virus buster 2011 cloud free trial


