Every time we give product training to sales people and technical people of various partner companies, we get various questions. When I was training the product the other day, I was told, "Do you need host-based intrusion prevention (IPS) for your PC? End users don't need extra features, so I don't want to add it if possible. I received the question.
Since it is a function installed in the product, it is installed because of course there is a need for security measures. Therefore, the reply is "a function necessary to prevent virus invasion and infection to PCs via LAN", but there are some related matters, so this time from this host-based intrusion prevention function. I would like to delve into the story.
Host-based IDS and IPS
I think that there are many companies that manage admission / admission at the entrance of the office, but it will be difficult to completely prevent unauthorized intrusion. Therefore, I think that there are cases where security cameras are installed in the office and, in some cases, a guard is placed to deal with unauthorized entry.
The same applies to the security of the corporate LAN. For security, it is desirable to use a function called host-based intrusion detection (IDS) or intrusion prevention (IPS) in addition to the personal firewall introduced last time.
Host-based IDSs monitor network connections coming into your PC (host) to identify unauthorized connections. You may think that a firewall can detect intrusions, but in reality, a firewall alone cannot completely prevent it. This is because the firewall allows communication from the permitted protocol / IP address (for example, the IP address in the company) even if the content of the communication is blocked.
Let's consider a case where a virus-infected in-house PC spreads to another PC via the in-house LAN. The virus makes numerous connections to other PCs in the company in a short period of time in an attempt to infect the virus. Even in this case, a firewall that only allows the connection according to the permitted port setting cannot determine whether the connection is malicious.
Even in these cases, it is host-based IDS that properly finds out if the communication to the host is a connection for a virus infection. It analyzes the connection pattern and notifies the user according to the settings if it is a suspicious connection pattern.

The firewall only establishes / denies connections according to the allow / deny list, it does not determine the connection pattern.
However, even if a host-based IDS issues a notification, it can be difficult for the user to determine if the content of the notification is really dangerous. Even if you contact the administrator, you may not be able to respond immediately, and in the meantime, the damage caused by the virus infection may spread.
Therefore, when a suspicious connection is detected, host-based IPS has a function to "may be a legitimate connection, but for safety, keep suspicious from passing through". Detects suspicious connection patterns and rejects connections according to your settings.
Intrusion Prevention (IPS) detects connection patterns and blocks connections with a "don't let suspicious" policy.
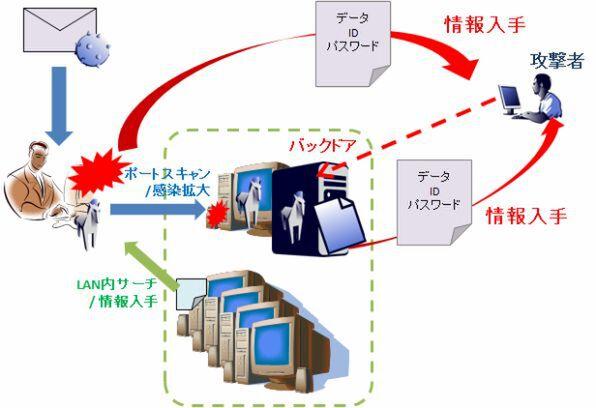
It is a targeted attack whose recognition rate increased at a stretch in the second half of 2011, but once infected with a PC, the malware used to search the PC in the LAN to collect information and scan the port in the LAN. .. It can then exploit the vulnerabilities of another PC to gain the necessary information and send it to an attacker, or open a backdoor to allow external control.
Port scan in LAN and use vulnerabilities to spread infection and obtain information
In this way, most of the malware that is active in the LAN uses the port scan method in the LAN to spread the infection and steal the in-house information. Therefore, for the network administrator in the company, the countermeasure against the port scan in the LAN is taken. Can be considered essential.
| TCP connect scan | A method for TCP ports is used to execute a SYN-SYN / ACK-ACK sequence called the 3WAY handshake, and check the status by checking whether a TCP connection can be established on the target port. |
|---|---|
| SYN scan (TCP half scan) | This is a method for TCP ports, and only the status of the target port is checked without establishing a connection.Check the status by sending a SYN packet to the target port instead of connecting.-The port when SYN / ACK is received from the target port is in LISTEN status.-The port when RST / ACK is received from the target port is in non-LISTEN status. |
| UDP scan | Since a connection cannot be established with UDP, a packet is sent to the target port, and if there is no response, it is judged as ACTIVE. If "ICMP port unreachable" is returned, it is judged as non-ACTIVE. |
Use firewall and IPS / IDS together
As mentioned above, since the firewall alone controls the connection only by the allow list / deny list, it does not judge whether it is a suspicious connection. For this reason, viruses and attackers trying to infect the LAN try to connect to the PC by port scanning etc. and grasp the status of the PC. I will try to attach using the weak part.
We recommend using host-based IDS or IPS in combination with a firewall from the perspective of preventing and countermeasures against the spread of virus infection in the LAN and information theft due to targeted attacks.
Make the most of the functions installed in the installed security products and keep them safe even in the LAN. Also, when selecting a security product, it is strongly recommended to look at the functions that can take security measures for the network from the viewpoint of protecting the PCs and servers on the LAN and the stored information. increase.
About the author: Yosuke Tomiyasu
F-Secure Co., Ltd. Technology & Service Department Product Expert Joined F-Secure in 2008. He is primarily responsible for technical assistance to partners for Linux products.


