On February 26th (US time), ESET reported the discovery of a bug "Kr00K (CVE-2019-15126)" that abused a particular Wi-Fi chip vulnerability.
Devices equipped with Broadcom and Cypress Wi-Fi chips are targeted, and these chips are mostly used in client devices such as PC in recent years. ESET has released vulnerabilities to both companies, and although patches from mainstream vendors have been released, they are also used by access points and routers, so even patches to client devices will be affected by the vulnerability.
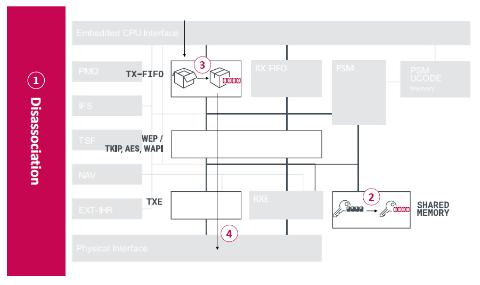
Kr00K, which is triggered by all-zero encryption key (all zero keys) used in communication between devices such as PC and access points, is a vulnerability that allows attackers to crack network packets of wireless communication and associate with "KRACK (Key Reinstallation Attack)" that exploits WPA2 encryption vulnerabilities.
Specifically, it is expressed when the "allocation association" of the session of the WLAN is cut off. At the time of allocation, a 128bit session key (TK:Temporal Key) for transmitting encrypted unicast data frames between devices is stored in the Wi-Fi chip, and the memory is cleared by a value of 0. So far, this is normal operation, but due to a failure, the data frame is left in the chip's send buffer and is sent after it is encrypted with all-zero encryption key. This allows an attacker to steal thousands of bytes of frames and decode them.
Kr00Kによってall-zero encryption keyで暗号化してデータを送信されてしまうIn addition, since no authentication or encryption is performed when associating / assigning an association, even if the attacker does not authenticate the WLAN connection, if the monitoring mode of WNIC (Wireless Network Interface Controller) is used, the association can be consciously initiated repeatedly. More frames can be obtained. As a result, the data with high concealment including the DNS/ARP/ICMP/HTTP/TCP/TLS packet is stolen.
ESET said that even if it is a conservative estimate, more than 1 billion Wi-Fi devices will be under the influence of Kr00K. Its tests include Amazon Echo (second generation), Kindle (eighth generation), iPhone 6/6S/8/XR, iPad mini2, MacBook Air Retina 13-inch 2018, Google Nexus 5max 6S, Samsung Galaxy S4 GT-I9505/S8, Xiaomi Redmi3S, Raspberry Pi3 and It is reported that the access points of Asustek and Huawei have re-emerged loopholes.
To prevent the impact of Kr00K, ESET reminds people to update and firmware updates to Wi-Fi-enabled devices such as PC/ tablets / smartphones / access points / routers.


